Dr. Henning Maier, Dr. Jasper Rödiger, Stefan Röhrich, all from Rohde & Schwarz
Whether it's private chat messages or government classified files, protecting data today almost always involves a combination of symmetric and asymmetric encryption. In symmetric encryption, the receiver decrypts the data with the same key that the sender used for encryption. The Advanced Encryption Standard (AES) uses this method and was certified by the National Institute of Standards and Technology (NIST) in 2000. It is now used worldwide.
Securing symmetric cryptography – asymmetrically
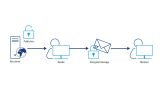
The critical issue in symmetric encryption is the secure distribution of keys between the communicating parties. Asymmetric encryption is normally used to protect key distribution. As the name implies, asymmetric key distribution uses a different key for encryption and decryption. A private key is kept confidential and a public key is provided with certified authenticity.
The public key can be transmitted in a public channel without any further protection. An important factor here is that the public key is one way: once data is encrypted, only a private key can decrypt it. The receiver initiates data transmission in the asymmetric encryption process (Figure). The strength of this method is that the sensitive private key remains with the receiver from the start and is not transmitted.
Since asymmetric encryption needs much more computing power than symmetric encryption, it tends not to be used for actual data traffic. Instead, the method secures the key distribution process for the symmetric encryption used for payload traffic.
Mathematical firewall
Since the public key is used for encryption, it also contains certain information about the decryption process. In principle, the private key can be deduced from the public key – but not within a reasonable amount of time. Public keys use mathematical problems that are difficult to solve, such as prime factorization or the calculation of discrete logarithms.
Deducing the private key would take an impossible amount of time. A conventional computer might need a few million years – or longer – to solve such problems.
Advanced quantum computers are a game changer
When advanced quantum computers are taken into consideration, the situation changes entirely. Shor’s algorithm was published back in 1994. It describes a method that significantly speeds up the factorization of prime numbers and the determination of discrete logarithms. It is a quantum algorithm that requires a quantum computer with sufficient computing power.
Since nearly all of the asymmetric cryptographic methods used today are based on these two mathematical problems, advanced quantum computers would rob them of their theoretical foundation. Although quantum algorithms are already known that can directly attack symmetric encryption methods, longer keys can preserve the level of protection here. However, no prior securing of key distribution is possible since the asymmetric encryption methods would be broken.
Experts at Germany’s Federal Office for Information Security (BSI) anticipate a 20 percent chance that the first quantum computers will be able to break currently secure encryption methods by 2030. Pressure is mounting to begin encrypting data with quantum-secure methods. This is especially critical for organizations and government authorities that handle larger quantities of sensitive data for extended periods of time. They will need a lot of time to convert the data they manage to quantum-secure encryption.
PQC and QKD: two methods with one goal
We currently have two promising quantum-secure encryption methods. In post-quantum cryptography (PQC), researchers develop special asymmetric algorithms impossible
to break within a reasonable amount of time, even with a quantum computer. Some promising candidates are based on diverse mathematical problems such as lattices or cryptographic hash functions. Another PQC approach uses error-correcting codes that a quantum computer supposedly cannot break efficiently.
One major advantage of PQC is that existing network infrastructure can continue to be used. However, certain challenges still remain. Some promising PQC candidates were recently broken. Furthermore, when compared to conventional asymmetric methods, PQC has problems with efficiency and key length. A lot of R&D effort is currently focused on these issues.
Quantum key distribution (QKD)
Quantum key distribution takes an entirely different approach. Certain fundamental laws of quantum physics are utilized to generate and securely distribute keys which can be used for symmetric cryptography. Instead of conventional bits, the communicating parties exchange qubits that are based on the quantum states of individual photons.
QKD has the advantage that individual quantum states cannot be perfectly copied and any third party trying to measure the photons to get their hands on a key can be discovered. These two fundamental laws of physics can be cleverly utilized to gain an advantage over a potential attacker. If the measured qubits are correctly postprocessed, a bit sequence can be generated that is known only to the two parties and can be used as a key.
If asymmetric cryptographic methods are broken, QKD can be a very important alternative. Quantum key distribution is based the laws of physics and information theory. The security of a key is independent of the processing power of quantum and conventional computers.
QKD-capable devices and infrastructure
Many QKD protocols are now available. In line with the principles described above, they are based on different degrees of freedom, including polarization as well as time and phase, and require different mechanisms to measure the quantum state. Some protocols are already well-developed and used in real applications. The first QKD solutions for secure point-to-point communications can now be purchased from a variety of suppliers. The range of available products will continue to grow in the near future.
Quantum encryption requires additional network infrastructure to transmit quantum bits. This infrastructure is currently being implemented in various regions around the world. The procedure is similar everywhere: individual point-to-point links are combined into larger test networks which are increasingly forming a commercially viable network. The largest QKD network is the quantum backbone network. It was officially completed in 2017 and has since been expanded across all of China.
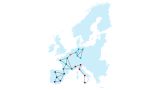
The European Union launched a program known as the European Quantum Communications Infrastructure (EuroQCI) initiative in 2019. Using optical fibers and satellite links, it will span the whole European Union, including overseas territories. The national networks created in this process will combine to form a common European network in the coming years.
QKD network elements
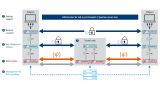
A quantum network is more than just QKD devices. It must also include hardened systems for key management, QKD-capable encryptors and control and management systems. Rohde & Schwarz Cybersecurity GmbH has recently become much more involved in the field. The company is working with various partners to develop functions and products – some of which can already be found in current solutions.
Rohde & Schwarz Cybersecurity has long been a trusted supplier of BSI-approved IT security solutions and can build on existing technology for conventional networks when developing QKD-capable encryptors. The functional range of these encryptors has been extended for use in QKD networks. They have been successfully deployed and are in continuous operation in European test networks as part of research projects.
Other technologies such as key management systems are being developed from the ground up. Rohde & Schwarz Cybersecurity expertise with hardened, approved security solutions is a major benefit since these systems need to be hardened for approval as well.